Patent Reform by Example – Tesla Opens Up Patents
Tesla Motors CEO Elon Musk announced in a blog post he has "Open Sourced" Tesla's electronic vehicle patents.
FBI Weighs Looser Pot Rules for New Hires – Funny
Fixing the “ACL found but not expected on …” error during OSX Volume Repair
Symptom – Running the OSX Disk Utility program and selecting Verify Disk permissions results is multiple error of ACL found but not expected on [filename]” While these errors can be safely ignored (ACLs are Access Control Lists) it does make reading the results of the disk verify difficult. Fix – Fletcher Tomalty has written a python script that can be run from the command line to remove these unexpected ACLs. The script uses the OSX Disk Utility to find the files and then does a sudo chmod -h -N on each of them. I have used it successfully on Mountain Lion 10.9.9.
FCC’s New Rules Could Threaten Net Neutrality
Federal Communications Commission Chairman Tom Wheeler is circulating a proposal for new FCC rules on the issue of network neutrality, the idea that Internet service providers (ISPs) should treat all data that travels over their networks equally. Unfortunately, early reports suggest those rules may do more harm than good. READ MORE
Why You Shouldn’t Put Your Money Where Your Mouth Is
By ROBERT LEE HOTZ
Wall Street Journal
April 18, 2014
Proposal to Prevent Grid Attack Lacks Power, Critics Say
A year after gunfire knocked out a substation that funnels power to Silicon Valley, the U.S. government has promised to make power companies amp up protection of equipment vital to the electric grid. Read full article at the WSJ
Viewing a winmail.dat Attachment
Problem – you receive an email that has an attachment named winmail.dat that your Mac Mail program can't view.
Reason – The Winmail.dat file is used in Outlook when sending a Rich Text-formatted message however OS/X Mail as the receiving client does not use or recognize the winmail.dat file format.
Solutions
Ask the sender of the email to change their default email settings. Microsoft suggests 4 methods here. Then have the sender re-send the attachment. This is often impractical as it places the burden on the sender who may be someone you don't want to burden. It also only the solves your problem with this one sender and not the hundreds of millions other of Outlook users.
There are well established technical standards for email and so it may seem unfair that you are stuck with this problem because Microsoft chose to use a proprietary format. Life isn't fair.
![]() It is faster and more practical to install an add-on to view winmail.dat files on a Mac. I use TNEF's Enough written by Josh Jacob.
It is faster and more practical to install an add-on to view winmail.dat files on a Mac. I use TNEF's Enough written by Josh Jacob.
Download the latest version, open the dmg file and drag the program into your applications folder. If you receive the occasional winmail.dat attachment, save it to your desktop, open TNEFF's Enough and select FILE -> OPEN, double click on the attachment listed in the TNEFF's Enough program window and select a save location. If you receive winmail.dat files often, drag the TNEFF app into your dock then drag the winmail.dat file from your email and drop it onto the TNEFF icon in your dock.
The Heartbleed Bug – What to Do Now

Websites that exchange sensitive information with users have, for many years now, secured the connection between a users browser and the web site by encrypting the information. The system is called SSL for Secure Sockets Layer and TLS for Transport Layer Security and up until the begriming of 2012 the software that implemented these techniques, OpenSSL protected the information as it flowed over the Internet by making it unreadable to anyone other than the intended recipient. A programming mistake (A missing bounds check) introduced into the software introduced a flaw in a function of the TLS protocol called heartbeat.
That flaw allowed a non-standard heartbeat command to return 64 KB or about 32 pages of text of unencrypted data. In effect, the programming error allowed an attacker to access the very information that SSL/TLS was intended to protect. Named for the heartbeat function that allows the data to be viewed by attackers, the bug has become known as Heartbleed.
What to Do Now
If you operate a website you have a great deal of work to do including updating the vulnerable Open SSL library, updating all the other system software and libraries that depend on that software, figuring out what software those changes broke and fixing them and revoking and reissuing new security certificates. If you're like most people you just want to know if some cyber-criminal has stolen the password to your online banking. The most conservative approach is to change all of your passwords once the websites you use have been protected from Heartbleed. Joseph Bonneau, a security researcher makes a good argument in Heartbleed and passwords: don’t panic that Heartbleed is not as catastrophic as the media reports would suggest.
If you want to be certain you should change all your passwords –
Step 1 – Test if the site has fixed the Heartbleed bug by going to https://www.ssllabs.com, enter the site URL and verify the test shows the site is not vulnerable to the Heartbleed bug.
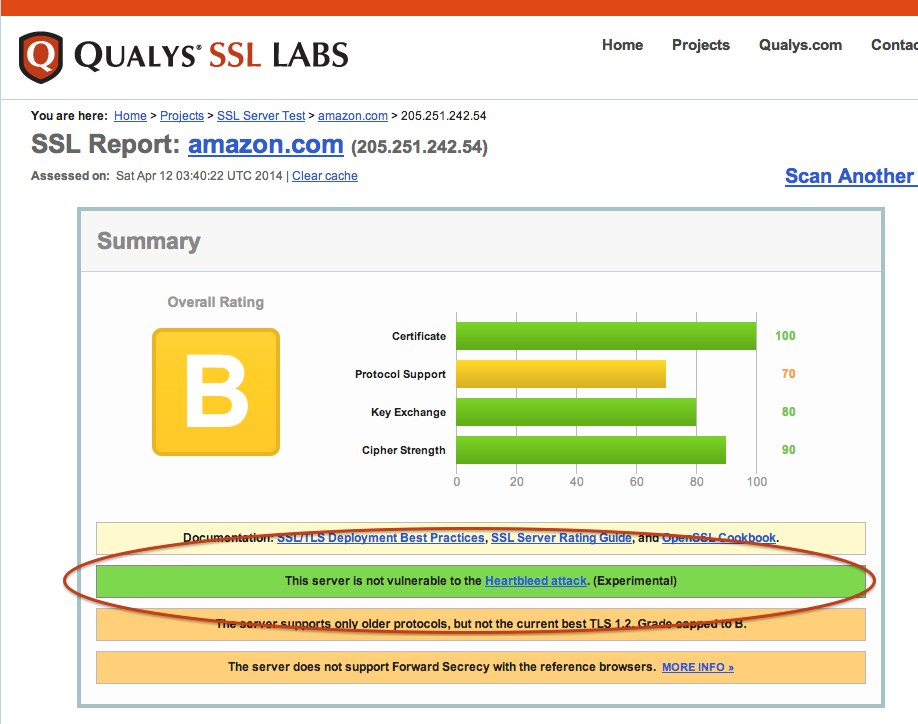
Step 2 – Change your password. As long as you are going to all the trouble of changing your password in every single site that you have a password, consider using good passwords and using them properly. You can read my take on good password hygiene here.
Repeat steps 1 and 2 for every site you have used. If you no longer use the site, login to it and delete your account.
If in the past you used the same password on multiple sites then you definitely need to change them anyway. Check back for my Password Pyramid approach.













