Category Archives: Uncategorized
Viewing a winmail.dat Attachment
Problem – you receive an email that has an attachment named winmail.dat that your Mac Mail program can't view.
Reason – The Winmail.dat file is used in Outlook when sending a Rich Text-formatted message however OS/X Mail as the receiving client does not use or recognize the winmail.dat file format.
Solutions
Ask the sender of the email to change their default email settings. Microsoft suggests 4 methods here. Then have the sender re-send the attachment. This is often impractical as it places the burden on the sender who may be someone you don't want to burden. It also only the solves your problem with this one sender and not the hundreds of millions other of Outlook users.
There are well established technical standards for email and so it may seem unfair that you are stuck with this problem because Microsoft chose to use a proprietary format. Life isn't fair.
![]() It is faster and more practical to install an add-on to view winmail.dat files on a Mac. I use TNEF's Enough written by Josh Jacob.
It is faster and more practical to install an add-on to view winmail.dat files on a Mac. I use TNEF's Enough written by Josh Jacob.
Download the latest version, open the dmg file and drag the program into your applications folder. If you receive the occasional winmail.dat attachment, save it to your desktop, open TNEFF's Enough and select FILE -> OPEN, double click on the attachment listed in the TNEFF's Enough program window and select a save location. If you receive winmail.dat files often, drag the TNEFF app into your dock then drag the winmail.dat file from your email and drop it onto the TNEFF icon in your dock.
The Heartbleed Bug – What to Do Now

Websites that exchange sensitive information with users have, for many years now, secured the connection between a users browser and the web site by encrypting the information. The system is called SSL for Secure Sockets Layer and TLS for Transport Layer Security and up until the begriming of 2012 the software that implemented these techniques, OpenSSL protected the information as it flowed over the Internet by making it unreadable to anyone other than the intended recipient. A programming mistake (A missing bounds check) introduced into the software introduced a flaw in a function of the TLS protocol called heartbeat.
That flaw allowed a non-standard heartbeat command to return 64 KB or about 32 pages of text of unencrypted data. In effect, the programming error allowed an attacker to access the very information that SSL/TLS was intended to protect. Named for the heartbeat function that allows the data to be viewed by attackers, the bug has become known as Heartbleed.
What to Do Now
If you operate a website you have a great deal of work to do including updating the vulnerable Open SSL library, updating all the other system software and libraries that depend on that software, figuring out what software those changes broke and fixing them and revoking and reissuing new security certificates. If you're like most people you just want to know if some cyber-criminal has stolen the password to your online banking. The most conservative approach is to change all of your passwords once the websites you use have been protected from Heartbleed. Joseph Bonneau, a security researcher makes a good argument in Heartbleed and passwords: don’t panic that Heartbleed is not as catastrophic as the media reports would suggest.
If you want to be certain you should change all your passwords –
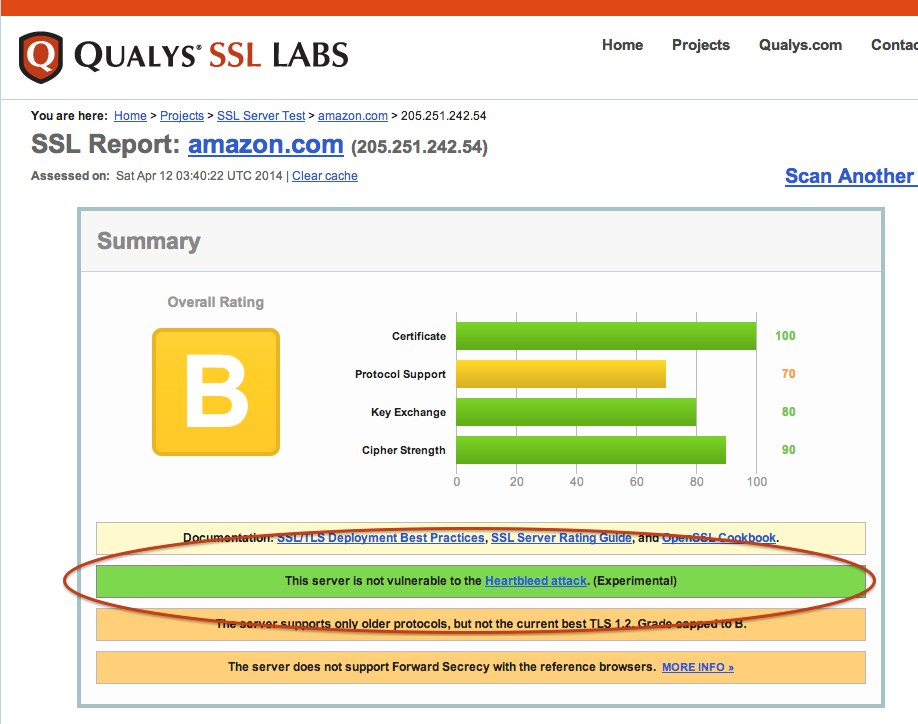
Step 1 – Test if the site has fixed the Heartbleed bug by going to https://www.ssllabs.com, enter the site URL and verify the test shows the site is not vulnerable to the Heartbleed bug.
Step 2 – Change your password. As long as you are going to all the trouble of changing your password in every single site that you have a password, consider using good passwords and using them properly. You can read my take on good password hygiene here.
Repeat steps 1 and 2 for every site you have used. If you no longer use the site, login to it and delete your account.
If in the past you used the same password on multiple sites then you definitely need to change them anyway. Check back for my Password Pyramid approach.
Windows XP Support Ends – Why You Need to Know
Alternatives
Disadvantages
- Learning Curve – OS/X is different than Windows and it takes some getting used to.
- Not all software runs on OS/X – if you absolutely must use a specific software title that is only available on Windows then stop reading now and go by a new PC.
- Apple hardware, in general, costs more than PCs that run Windows.
- There are far fewer viruses for Macs than PCs. While this may not always stay true, the vast majority (over 99%) of viruses target Windows PCs. Mac users spend a lot less time on ant-virus software updates and cleaning out infections that get through.
- Apple has always been something of a control freak when it comes to their products. An upside of this is that most software that runs on Macs follows a consistent user interface. In general, the way you do things is pretty consistent between programs and inter-program communication tends to be excellent.
- Ease of Use – I know that this is subjective however having used both systems for years I come down solidly on the side of Macs.
- Files created on one can not be used on the other – FALSE
- It is hard to get technical support for Macs – FALSE on two levels, there are plenty of Mac gurus out there and Mac users need a lot less support.
- I need to use Microsoft Office so I can’t use a Mac. FALSE – Microsoft Office for Mac is, with very few exceptions is compatible with the PC versions. There are some Macro language and VBA differences that should only be an issue in a large corporate environment with dozens of connected spreadsheets tied together.
New Medium Troy Video
Teaser video for Bohemian Dub Orchestra project
NSA surveillance program reaches ‘into the past’ to retrieve, replay phone calls
The National Security Agency has built a surveillance system capable of recording “100 percent” of a foreign country’s telephone calls, enabling the agency to rewind and review conversations as long as a month after they take place, according to people with direct knowledge of the effort and documents supplied by former contractor Edward Snowden.
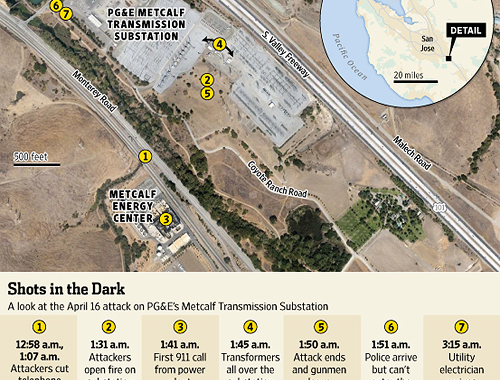
Assault on California Power Station Raises Alarm on Potential for Terrorism
NSA Gadget Catalog – Stuff You Won’t See at CES
After years of speculation that electronics can be accessed by intelligence agencies through a back door, an internal NSA catalog reveals that such methods already exist for numerous end-user devices. Read the full article here.
Codeacademy – Learn to Code
Take up the President's call to code – create a a free account at Code Academy and learn to code. Stop complaining about buggy software and write your own health care exchange.