Websites that exchange sensitive information with users have, for many years now, secured the connection between a users browser and the web site by encrypting the information. The system is called SSL for Secure Sockets Layer and TLS for Transport Layer Security and up until the begriming of 2012 the software that implemented these techniques, OpenSSL protected the information as it flowed over the Internet by making it unreadable to anyone other than the intended recipient. A programming mistake (A missing bounds check) introduced into the software introduced a flaw in a function of the TLS protocol called heartbeat.
That flaw allowed a non-standard heartbeat command to return 64 KB or about 32 pages of text of unencrypted data. In effect, the programming error allowed an attacker to access the very information that SSL/TLS was intended to protect. Named for the heartbeat function that allows the data to be viewed by attackers, the bug has become known as Heartbleed.
The bug was first reported to OpenSSL by Neel Mehta from Google Security Matti Kamunen, Antti Karjalainen and Riku Hietamäki from Codenomicon Oy and was reported publicly by the group that wrote OpenSSL on April 7, 2014. The notice itself may well be one of the most understated alerts in the history of computer security with no mention of the catastrophic impact on the Internet and Online commerce. A conservatively estimated is that two-thirds of the Internet's Web servers use OpenSSL to cryptographically prove their legitimacy and to protect passwords and other sensitive data from eavesdropping. Many more e-mail servers and end-user computers rely on OpenSSL to encrypt passwords, e-mail, instant messages, and other sensitive data.
What to Do Now
If you operate a website you have a great deal of work to do including updating the vulnerable Open SSL library, updating all the other system software and libraries that depend on that software, figuring out what software those changes broke and fixing them and revoking and reissuing new security certificates. If you're like most people you just want to know if some cyber-criminal has stolen the password to your online banking. The most conservative approach is to change all of your passwords once the websites you use have been protected from Heartbleed. Joseph Bonneau, a security researcher makes a good argument in Heartbleed and passwords: don’t panic that Heartbleed is not as catastrophic as the media reports would suggest.
If you want to be certain you should change all your passwords –
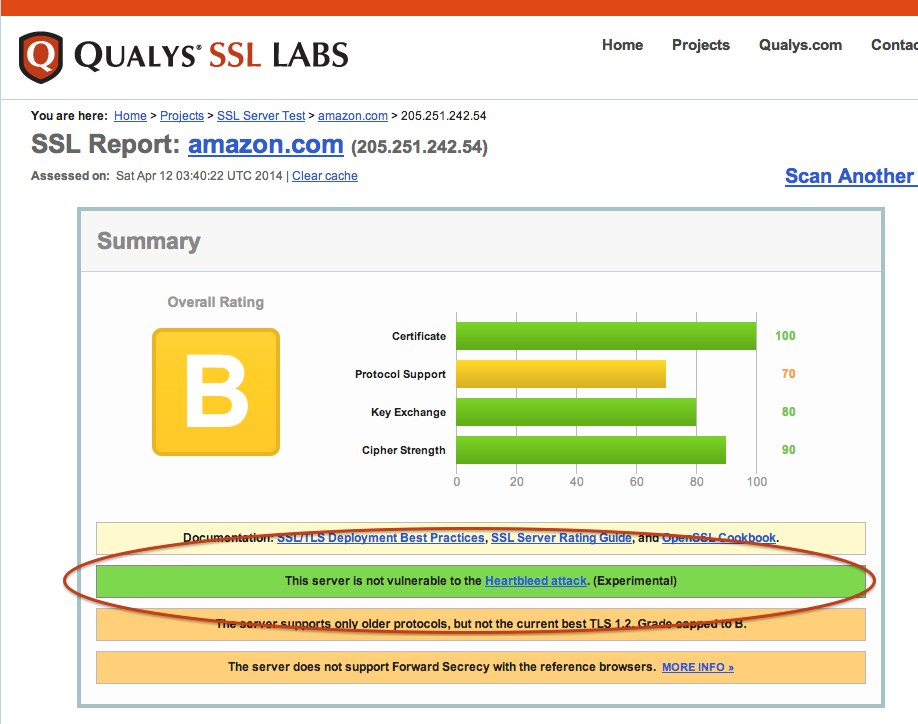
Step 1 – Test if the site has fixed the Heartbleed bug by going to https://www.ssllabs.com, enter the site URL and verify the test shows the site is not vulnerable to the Heartbleed bug.
Step 2 – Change your password. As long as you are going to all the trouble of changing your password in every single site that you have a password, consider using good passwords and using them properly. You can read my take on good password hygiene here.
Repeat steps 1 and 2 for every site you have used. If you no longer use the site, login to it and delete your account.
If in the past you used the same password on multiple sites then you definitely need to change them anyway. Check back for my Password Pyramid approach.

![]() It is faster and more practical to install an add-on to view winmail.dat files on a Mac. I use TNEF's Enough written by Josh Jacob.
It is faster and more practical to install an add-on to view winmail.dat files on a Mac. I use TNEF's Enough written by Josh Jacob.